Ordered a burrito and bowl of soup, cost $12.
Original meme created 29 AUG 2021.

Ordered a burrito and bowl of soup, cost $12.
Original meme created 29 AUG 2021.
I needed to update a Cpanel Dynamic Domain Name Service (DDNS) entry automatically for a virtual machine (VM) that I manage, to allow a simple address to type rather than obtaining the new dynamic host configuration protocol (DHCP) from the VM’s command-line interface (CLI).
Our first step is to log on to the hosting domain’s Cpanel interface and select “Dynamic DNS” under the domains section. Then select “Create”. Here you will create the subdomain prefix for the new address you wish to be updated. Leave the “manually enter an IP address blank” as we will use this for testing later.
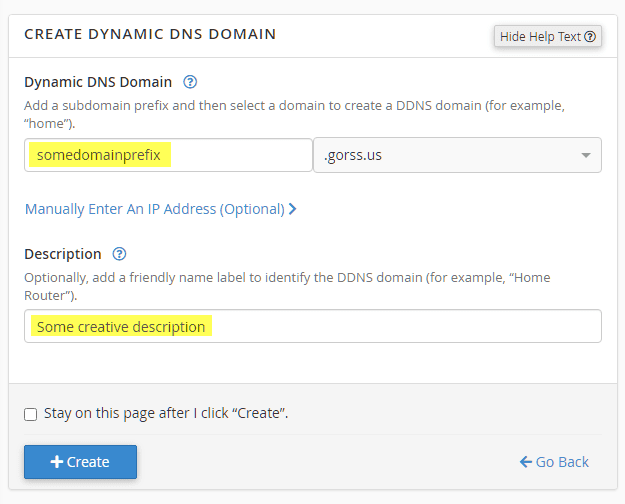
After the subdomain is created, you will be taken to the list page showing the new entry. Leave this page open, as you will need to copy the URL that is shown to copy into CentOS later and will use it to verify the updates are taking place.
Now log in to your CentOS server using an SSH interface. If you don’t have an SSH client, PuTTY has been around for ages and works quite well. The steps that follow next are for CentOS 7 or 8, using the systemd unit and nano editor. Every Linux admin has their preference for editors, mine happens to be nano.
sudo su - root sudo nano /etc/systemd/system/updateddns.service
You will need to enter the URL from the Cpanel DDNS page we left open before under the [Service] section. You can copy and paste the data below to save time.
[Unit] Description=Update Cpanel DDNS Requires=network-online.target After=network-online.target [Service] ExecStart=/usr/bin/curl https://gorss.us/restoftheurlhere [Install] WantedBy=multi-user.target
After the creation of the service and entering your Cpanel DDNS update URL, you will need to create the startup.
sudo systemctl enable updateddns.service
Now, this should start the service automatically upon server reboot. However, depending on your server’s security setup, your user account may not have permission to start services without entering a password. We can test this by trying to start the service manually.
sudo systemctl start updateddns
If you receive a prompt for a password, you will need to edit another file and give your sudo user account the NOPASSWD switch for this service. In the directions which follow, the “sudouser” is the name of the account you use for the sudo account; typically this means root is disabled at the command line and is a good security practice.
sudo visudo
Scroll to the end of the file and enter the following, using your sudo user account; again sudouser here is just a place setter and not the actual user.
sudouser ALL=NOPASSWD: /bin/systemctl start updateddns, /bin/systemctl stop updateddns, /bin/systemctl restart updateddns, /bin/systemctl status updateddns
Save the file, then switch to your sudouser account and test the commands again. You should no longer receive a prompt for a password, this will now let the updateddns service run on server reboot/startup.
su - sudouser sudo systemctl start updateddns sudo systemctl stop updateddns sudo systemctl restart updateddns sudo systemctl stop updateddns
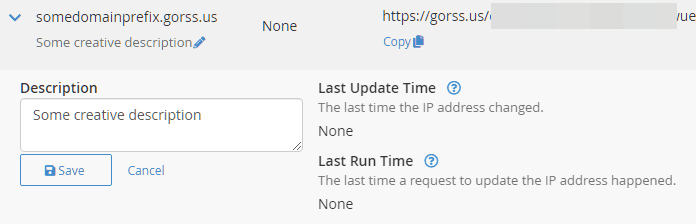
You can now check the Cpanel DDNS interface page we left open earlier, refreshing the page, and it should indicate the last update to the record.
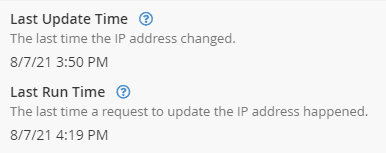
You could also ping the new subdomain to validate the change also. If your primary domain name has been live for over 48-hours, the new subdomain should resolve immediately.

Gave this frosting a whirl today, ran the mixer on high for a good few minutes and it’s better than most store bakery versions. Was excellent on spice cake!

You can find the receipe here: https://www.allrecipes.com/recipe/8379/basic-cream-cheese-frosting/
While trying to take a photo of the moon yesterday, it came out hazy due to the weather. Today though, it came out great. The details when I zoom in are just spectacular. Not bad for a first attempt with a DSLR. Noticed the image quality was a bit downgraded after upload, but the lower corner of the moon still looks sharp!
Mobile searches are just as important as the desktop search. If you are selling a service or marketing a client who sells locally, your mobile search is even more important. People will often search on their phone to find something nearby, why not make sure you’re taking advantage of it?
You can read more about Google’s mobile-first indexing via the link below, or you can check your site for mobile-friendliness now via this link.
Official news on crawling and indexing sites for the Google index
Source: Official Google Webmaster Central Blog: Getting your site ready for mobile-first indexing
Using NMAP can help identify vulnerable points on your network. One of the more effective tools out there, and as usual, the best are the command line. – AG
Nmap command examples and tutorials to scan a host/network, so to find out the possible vulnerable points in the hosts and secure the system.
Source: Top 32 Nmap Command Examples For Sys/Network Admins – nixCraft

Back in August a version of CCleaner was released that was infected. More information is available around the web, but the direct release from Piriform is here. Recently Piriform was acquired by Avast.
For the full technical details, you can read this post, which contains all the information for hashes, registry entries, etc.